TryHackMe - Bounty Hacker Room
Another box down! This is so much fun! I think I'm really starting to get the hang of it. This was the Bounty Hacker box, themed after Cowboy Beebop.
Reconnaissance
The default website has some fun story text.
The themeing here is great as I'm a big anime fan myself. It's running Apache 2.4.18 on Ubuntu as per our developer tools in the browser.
And since there's no other hints here, we're on to enumeration.
Enumeration
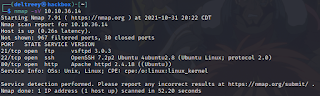
We start with nmap as it is the standard.
I noticed FTP is open. That could be useful later. Let's check out gobuster.
I wonder if this images directory has anything interesting.
Meh, not much here. Ok, let's see if we can exploit the FTP server.
Exploitation
FTP on port 21 is insecure, so let's see if it will let us login as anonymous.
It sure does and there's some files here. Let's grab those. On FTP, you use the GET command to do that.
Alright, let's see what's in these files.
Well, I don't know what the task list is about, but this is the answer to the question about who wrote it, and it also looks like a username.
This locks.txt file looks like a list of passwords actually. With a username and a password, let's take a closer look at the ssh server. I don't have a screenshot, but when I tried to SSH as lin, it asked for a pasword. This is great. It means that the SSH doesn't require a private key, but just a password. Cool. Let's try this password list with hydra.
Hydra seems to have identified our password for lin. That tells us the answer to the next question. We can bruteforce ssh with the text file. Let's see if we can login with it.
Woohoo! We made it! We now have the answer to the user's password. Let's see if we can find the flag.
Easy Peasy! Onto Privilege Escalation.
Privilege Escalation
Well, let's take a peek at our sudo abilities. I don't want to make the same mistake as last time.
Well that paid off. We have sudo for root over the tar binary. Let's head to GTFOBins.
Success: https://gtfobins.github.io/gtfobins/tar/#sudo Let's run it.
Success! We have rooted the box. Let's find our last flag.
Man this is the best! I'm thoroughly enjoying myself.
















Comments
Post a Comment